Not known Facts About Aws Backup
Some Known Details About Aws S3 Backup
Table of ContentsUnknown Facts About Data ProtectionTop Guidelines Of Aws BackupThe 7-Minute Rule for Data ProtectionThe 15-Second Trick For Aws S3 BackupThe Best Guide To Aws Cloud BackupRansomware Protection for Beginners
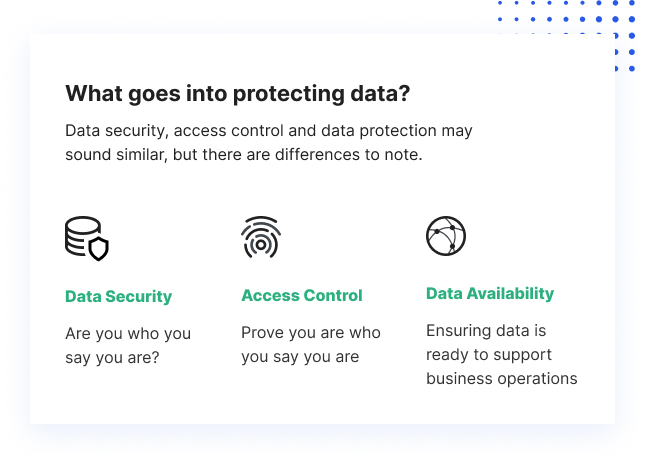
Data security is the process of protecting vital info from corruption, compromise or loss - https://www.ted.com/profiles/39538318/about. The relevance of data defense raises as the quantity of information developed as well as stored remains to grow at unprecedented rates. There is likewise little tolerance for downtime that can make it difficult to gain access to crucial details.Protecting data from compromise and ensuring information personal privacy are various other essential components of data defense. The coronavirus pandemic created numerous employees to work from home, leading to the demand for remote information defense (https://ouo.press/lTj8LKY). Companies need to adapt to ensure they are securing information anywhere employees are, from a main information facility in the workplace to laptops in the house.
The essential principles of information defense are to secure and offer data under all conditions. The term data protection describes both the functional backup of information as well as service continuity/disaster healing (BCDR). Data security methods are advancing along two lines: information availability and data monitoring. Information schedule guarantees customers have the data they need to carry out organization even if the data is harmed or shed.
Data lifecycle administration is the process of automating the motion of vital data to online as well as offline storage space. Info lifecycle monitoring is a thorough approach for valuing, cataloging and also securing information properties from application and also user errors, malware as well as virus attacks, device failing or center outages as well as interruptions. More recently, information monitoring has actually involved include discovering methods to open organization value from otherwise inactive duplicates of data for reporting, test/dev enablement, analytics and other purposes.
The Only Guide for S3 Cloud Backup

Information was occasionally duplicated, usually each night, to a disk drive or tape library where it would certainly rest until something went incorrect with the main data storage space. That's when companies would certainly access and utilize the back-up information to bring back shed or damaged information. Back-ups are no more a standalone function.
See This Report on Ec2 Backup
Back-up's purpose was to recover information after a failure, while an archive supplied a searchable duplicate of data. That led to repetitive information sets.

Pictures and duplication have actually made it possible to recuperate much quicker from a calamity than in the past. When a server stops working, information from a backup range is utilized in area of the primary storage space-- but only if a company takes actions to avoid that backup from being changed.
The initial data from the back-up variety is then used for checked out procedures, and create operations are routed to the differencing disk. This approach leaves the original back-up data the same. As well as while all this is occurring, the stopped working web server's storage space is restored, and also information is replicated from the backup array to the stopped working server's recently reconstructed storage - https://writeablog.net/clumi0/h2-style-clear-both-id-content-section-0-what-does-protection-against.
Our Aws S3 Backup Ideas
Information deduplication, likewise known as data dedupe, plays a vital duty in disk-based back-up. Dedupe applications change redundant data obstructs with reminders to one-of-a-kind information copies.
Deduplication began as an information security innovation and has relocated right into main data as an important feature to lower the quantity of capability required for more costly flash media. CDP has pertained to play a vital function in catastrophe healing, as well as it makes it possible for quick restores of back-up data. Continual data protection allows companies to roll back to the last excellent duplicate of a file or data source, decreasing the quantity of information lost in the instance of corruption or data removal.
CDP can additionally remove the need to keep several copies of information. Rather, companies retain a solitary duplicate that's upgraded continuously as changes take place.
Synchronous matching is one strategy in which information is click here now contacted a local disk and a remote site at the same time. The compose is ruled out full until a confirmation is sent from the remote site, guaranteeing that the 2 sites are always similar. Mirroring calls for 100% capacity expenses.
The 25-Second Trick For Aws Cloud Backup
The price of recouping from a media failing is the moment it requires to go back to a safeguarded state. Mirrored systems can return to a secured state rapidly; RAID systems take longer because they should recalculate all the parity. Advanced RAID controllers don't have to review a whole drive to recuperate data when doing a drive rebuild.
Like RAID, erasure coding uses parity-based information defense systems, writing both information and also parity across a cluster of storage nodes.
Duplication is one more information defense alternative for scale-out storage space, where information is mirrored from one node to one more or to multiple nodes. Duplication is easier than erasure coding, but it consumes at the very least twice the capacity of the safeguarded information. With erasure coding, information is kept throughout different disks to shield versus any solitary point of failing.
Unknown Facts About Rto
A lot of storage systems today can track hundreds of photos with no substantial impact on performance. Storage space systems making use of pictures can collaborate with systems, such as Oracle as well as Microsoft SQL Server, to catch a clean duplicate of information while the snapshot is occurring. This strategy allows regular snapshots that can be saved for extended periods of time.
With this technique, minimal information is lost and also healing time is practically instantaneous. To shield against numerous drive failures or a few other major occasion, data facilities depend on replication modern technology built on top of photos. With picture duplication, only obstructs of data that have changed are copied from the key storage system to an off-site second storage space system.